Training
The following content will give you an introduction to code-signing certificates. It will help you discern what should be reported.
The following is a lot of text. However, if you are interested in more interactive content, check out Squiblydoo's free VirusTotal Fundamentals course on KC7Cyber. The course is fun but provides a vital introduction to VirusTotal as well as code-signing certificate abuse.
What is a Code-Signing Certificate?
A code-signing certificate is a digital certificate that is used to sign software executables and scripts in order to verify the author's identity and ensure that the code has not been altered or corrupted since it was signed.
This training only pertains to certificates that are issued by a certificate provider. When a certificate provider issues a certificate, they co-sign the software as an attestation that they have validated that the signer is a legitimate organization and software provider. This signature confers trust from the issuer to the signer. On the other hand, a self-signed cert does not confer trust from one organization to another. As a result, self-signed certs indicate that the signer trusts themselves: as they are both the signer and issuer. These self-signed certs are not interesting for the purpose of this discussion.
Because code-signing confers trust, both operating systems and browsers will check to see if downloaded files are signed with a code-signing certificate. If the file is issued by a trusted party (a certificate provider), the browser and operating system will trust the file.
This transfer of trust is what is important for malware distributors and it is why code-signing certificates are important.
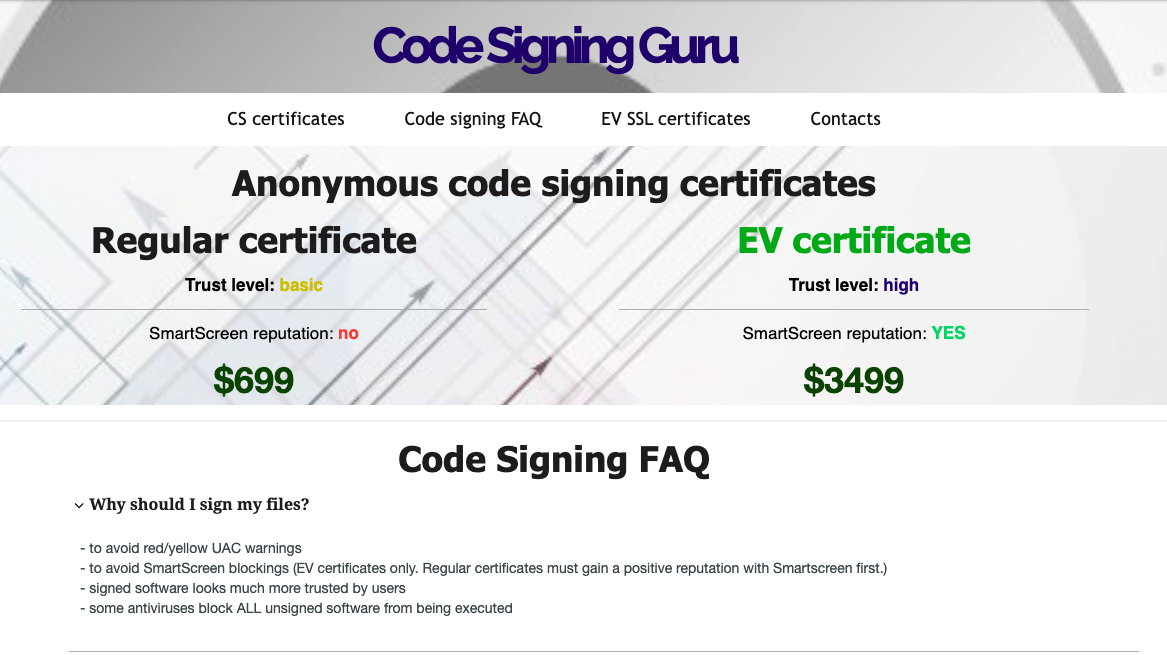
When criminals advertise the sale of code-signing certificates they mention the trust it will receive. This type of trust transference is also seen in the advertisements. In the advertisement below, the seller states that Extended Validation (EV) certificates have a high trust. The trust from the certificate allows it to have a good reputation with SmartScreen, browsers, and it prevents warnings from Windows User Account Control (UAC).
How do attackers get certificates?
Criminals apply for the code-signing certificate themselves and receive them. Based on research from 2018 and Squiblydoo's observations since then, this is the most common way for actors to obtain code-signing certificates.
The application for a code-signing certificate requires several validation steps and is an in-depth process.
How do you identify a file is signed?
For the purposes of this website, I recommend reviewing a report of the file in VirusTotal or on MalwareBazaar.
In the sections below, we will discuss how to identify a signed file on each platform and the different statuses that a certificate can have.Signatures on VirusTotal
On VirusTotal, you can view the signatures of a file by clicking on the Details tab. The Details tab will show you the signatures of the file. If the file is signed, you will see the signature in the Signers section.
Below is an example of a signed file on VirusTotal. The file is signed by TOV "SELT MOTO" and the signature is valid.
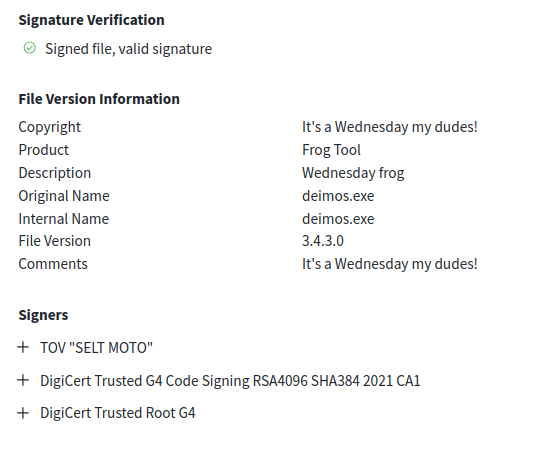
VirusTotal uses Microsoft's SigTool to extract the certificate information. VirusTotal provides the status of the certificate on the page. The main statuses are Valid, Invalid, Not Time-Valid, and Revoked. Valid, Not Time-Valid, and Revoked all indicate that the signature had been properly signed. Invalid indicates that hash in the signature does not match the hash of the file: this indicates that the file has been altered since it was signed or the certificate does not belong to this file. These statuses are discussed in more depth below. In addition to the signature section, VirusTotal also provides information about the certificate in the file "tags" seen at the top of an analysis. In the image below, the file is tagged as "signed" and "invalid-signature".
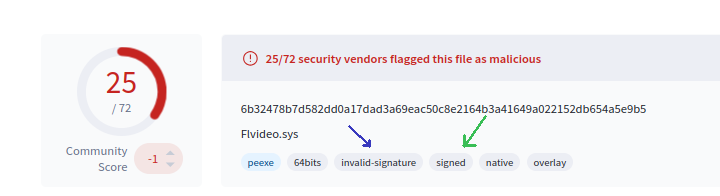
Find the current status of the certificate pictured above.
Signatures on MalwareBazaar
On MalwareBazaar, you can view the signature on the main page of the file analysis in the "Code Signing Certificate" section. Unlike VirusTotal, MalwareBazaar does not display the current status of the certificate. They do not display certificates that are Invalid.
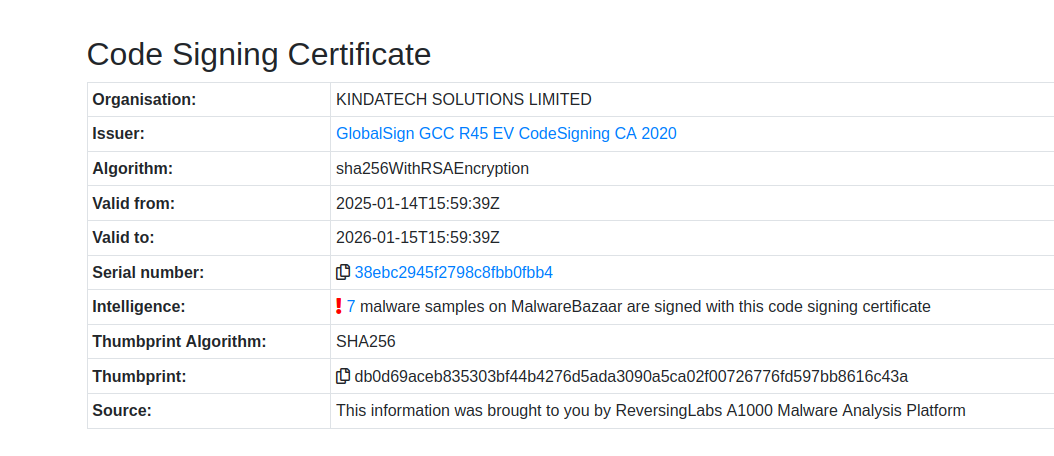
MalwareBazaar relies on ReversingLabs A100 to extract information regarding the certificate. A newly submitted file may take a few minutes for the certificate to display on the page.
Identify the organization that signed this file on MalwareBazaar.
What are the different certificate statuses?
When a file is signed, the signature can be in one of four states: Valid, Invalid, Not Time-Valid, or Revoked.
- When a signature is Valid, this indicates that the signer has control of the keys to sign files and the file is correctly signed.
- When a signature is Invalid, this indicates that the file doesn't have a valid certificate. The file may have been altered after signing or the certificate may have been taken from one file and put on another.
- When a signature is Not Time-Valid, the certificate may have been valid in the past, but the certificate is now no longer within the validity period. Certificates are only valid for a certain duration, usually 1 to 3 years.
- When a signature is Revoked, the certificate has been revoked by the certificate provider. This means that the certificate is no longer trusted and the certificate was used maliciously.
What are important parts of a certificate?
Below are the components of a certificate. These components are important to understand when identifying malicious certificates and reporting them.
- Signer: The organization that was issued the certificate and signed the file.
- Issuer: The organization that issued the certificate to the signer. In cases where the Signer and Issuer are the same, it is considered a self-signed certificate. This training and the website do not consider self-signed certificates interesting.
- Serial: The serial number of the certificate. This serial number uniquely identifies an individual certificate. Signers may be issued multiple certificates so the serial number and thumbprint can help distinguish them.
- Thumbprint: The thumbprint is a hash of the certificate. This hash is unique to the certificate and can be used to identify the certificate.
- Valid From: The date the certificate begins to be valid.
- Valid To: The date the certificate stops being valid. All certificates have a validity period.
How can you identify a malicious certificate?
Multiple indicators can help identify a malicious code-signing certificate. The most common indicators are:
- If the file, on its own, performs malicious behavior, it is a malicious certificate.
- For example, this file was signed and was observed dropping a NetSupport, a Remote Management and Monitoring (RMM) application. This behavior was observed in a sandbox and also identified by multiple detection rules on VirusTotal.
- If the file requires additional files, like a DLL, to be present to perform the behavior, this is an indication that the file may be performing DLL Search Order Hijacking. In these cases, the EXE may be signed but is not itself malicious; it is only vulnerable to this technique. These certificates should not be reported.
- One common indicator of this is that the EXE has a clean VirusTotal reputation, that is, it is detected as benign by all detection engines.
- Another indicator is that the file has been uploaded to VirusTotal with a large number of different names.
- We often see PDF viewer tools being used to perform DLL hijacking. In these instances, the user will receive a ZIP file that contains the legitimate EXE and malicious DLL. The ZIPs can be seen as Execution Parents in the "Relations tab" on VirusTotal.

- If the file version information or other details appear inconsistent with the certificate signer, it may be a malicious file. This should be confirmed with other suspicious or malicious behavior.
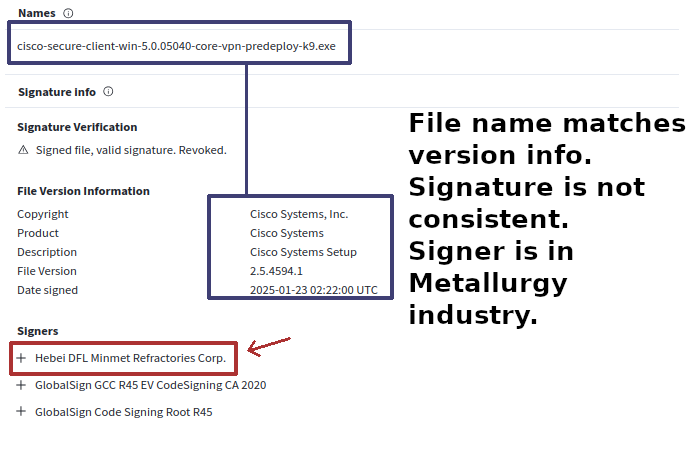
Not all cases are easily identified. Some malware may have a low detection score on VirusTotal and may require manual malware analysis and an investigation to identify the malicious indicators.
In one recent instance, we identified a software named "PDFSkills" which uploaded user files to their servers; this behavior was in contradiction with their stated Terms of Service. Upon further investigation, we found that the code-signing certificate was issued to an organization which could not be found to be associated with PDFSkills. This inconsistency was further confirmed after the first certificate was revoked and a new certificate was used with a different organization name. For more details on this example, see this BlueSky post: https://bsky.app/profile/squiblydoo.bsky.social/post/3ldqqqzrhpk26
Should Potentially Unwanted Programs/Applications (PUP/PUA) or Adware be reported?
No. PUP/PUA and Adware are not considered malicious. These programs are often installed with the user's consent. They are not considered malicious because they do not perform malicious behavior. They may be unwanted, but they are not malicious. However, it is important to investigate whether the software is performing malicious behavior. Some malware will install freeware or PUP as a decoy to distract from the malicious behavior. In these cases, the freeware should be reported. In most cases, the code-signing certificate will be consistent with the PUP/PUA. In these instances, the certificate is not considered malicious.
I understand all of the above, but how do I report?
To report code-signing certificates you have a few options.
- Log into The Cert Graveyard, and use the submit form. When submitting with this form, we take care of the contact with the certificate provider for you.
- Use a command-line tool we provide: certReport. More information about using these tools is available here. An in-depth explanation of certReport is available on the Squiblydoo blog.
- certReport - creates a report for you to send to the certificate provider and it tells you where to send it.
- certReportCentral - sends the information to The Cert Graveyard and we take care of the report for you.